VPLM Client/Server Introduction | ||
| ||
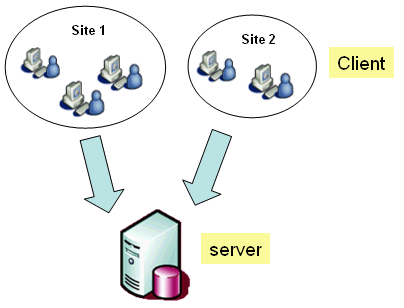
Client/Server Architecture
This architecture enables customers to share the same data inside the same site, and through different sites. When the enterprise is multi-site or when an enterprise works with multiple suppliers, distributed data processes can be supported.
This digram reprsents the client/server architecture;
The picture below presents the ENOVIA V6 server:
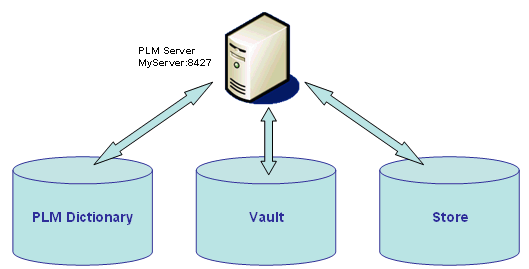
The PLM Server is based on three parts: (blue cylinders are part of the PLM Server).
- PLM Dictionary contains metadata required by the PLM Server to structure the Vault database.
- Vault lies on an Oracle, DB2 or MS SQL Server Database. Its data are defined by the dictionary metadata
- Store is a file server containing binary files pointed by the data contained in the Vault
![]()
PLM Dictionary
PLM server cannot access to the vault without having information about the data structure. This information is given by the PLM Dictionary.
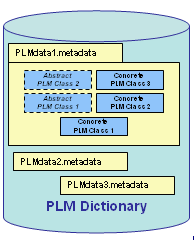
The PLM Dictionary is a build time information initialized during the installation of the server. It contains the description of all the types (PLM Classes) of PLM entities along with their attributes and relations. The PLM Classes are grouped together into modelers (.metadata files).
To simplify, each metadata file describes a PLM Modeler. The metadata contains a set of entities, named PLM Class, describing each one an element of the PLM Modeler. Some PLM Classes are concrete, they could be instantiated in the database, or abstract otherwise.
A PLM Class has PLM Attributes and PLM Relations.
![]()
Vault (the Database)
The Vault is the database containing entities, called PLM Objects, created from concrete PLM Classes defined in the PLM Dictionary.
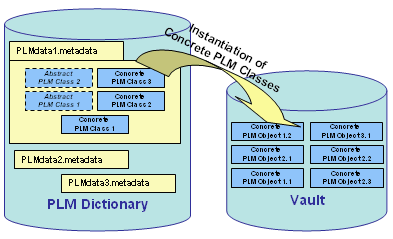
This figures shows two instances ( PLM Object 1.1 and PLM object 1.2) of the same prototype (i.e. PLM Class) PLM Class 1 .
A PLM object is an instance of a PLM Class; therefore it benefits from its PLM Attributes and PLM Relations. The PLM Attributes will be evaluated during the instantiation or later.
![]()
Store (the File Server)
PLM Attributes are fine to describe small, simple queriable information such as strings or integer values, but larger information set also have to be associated to PLM entities.
Here are two examples:
- Geometry, which is defined by features, as shown by this 3D geometry represented in a 3D viewer.

- Computed results, or data stored as Word, XLS, or text files:
To release these kind of associations, some PLM object could point files within a file server, named store. There are binary files also named stream .
Notes:
- PLM Representation Reference can point to a stream.
- A file cannot be opened without loading in session the PLM Representation Reference itself (vault attributes).
- A PLM object can point to several streams, but only one called the main stream. The other streams, named secondary streams, are generated and only used internally.

![]()
Secure Connection
As any connection to a server, end users must enter usernames and passwords.
To enforce the security, we have added other information, that we named the PLM Security Context:
- Role
- Organization
- Project
Accordingly, some PLM objects in the database are not accessible to a user when connected with these parameters.
Example: Imagine a shipbuilding company. Some people work on the hull, and others on the engines. You assign the Hull project to the first team, and the Engine project to the second one. Someone on the Hull team cannot access the data (PLM objects) for the Engine project. This project structure lets you restrict access to the Engine data by the Hull team and vice versa.
![]()
PLM Server Access
This graphic shows the complete client/server architecture.
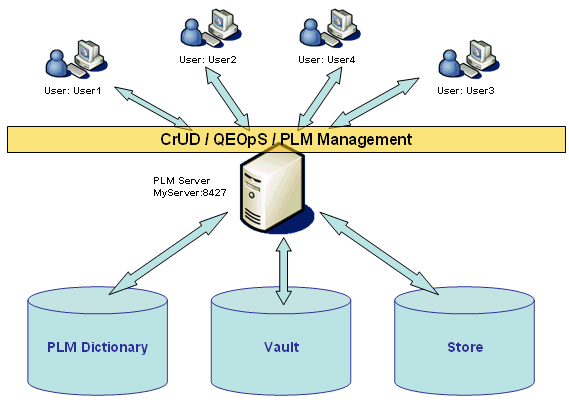
This diagram shows that all server accesses are done through a unique layer. This unique layer is based on a set of operations:
- Creat, Update Delete (Crud) operations
- Query Expand Open Save (QEOPS) operations
- PLM management operations (versioning, lock, change maturity (lifecycle operations))
Other client operations (rename, replace, change attribute values) are described to the server through this minimal set of operations. In addition, all QEOPS and PLM Management operations take into account the PLM Security context.