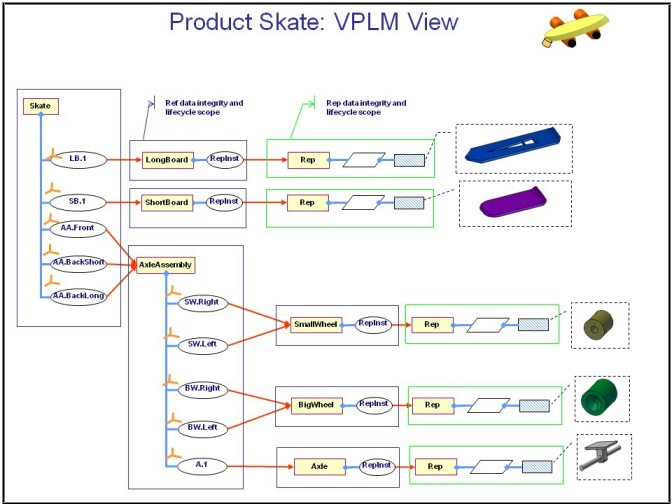
Implementing Security on Instances | ||
| ||
![]()
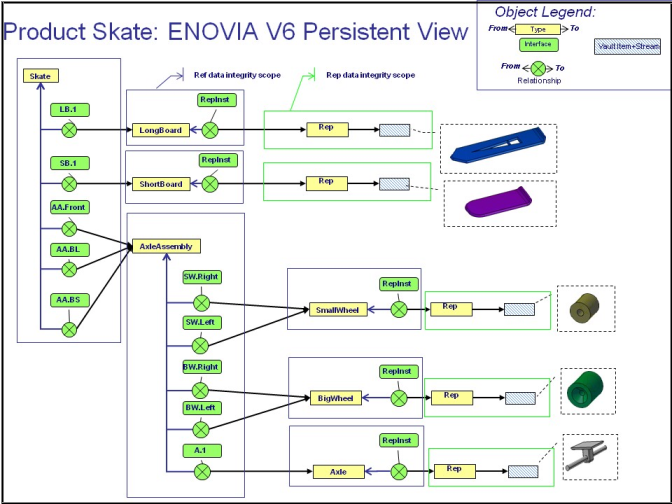
ENOVIA V6 World
And this is how the same VPLM instance is represented in the ENOVIA V6 types/relationships/interfaces model:
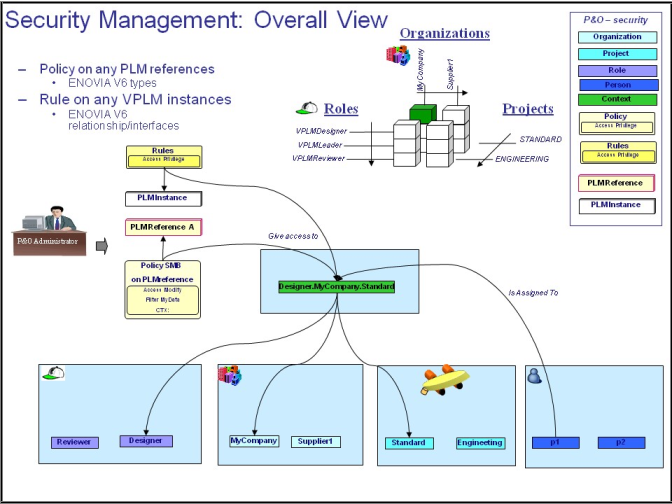
From the following diagram, we can see how the overall security mechanisms all fit together:
- policies govern access to PLM References
- rules govern access control to PLM Instances via ENOVIA V6 relationships/interfaces
![]()
A Simple Example: Expand Operation
For illustration purposes, the following diagram concentrates on one instance and shows how a typical access control rule is expressed first of all using a natural VPLM language, then in the language used in ENOVIA V6 rules.
Warning: the syntax of the rule in this diagram is for illustration purposes only.
The PLM instance to be expanded is Instance left wheel.
Expressed in natural VPLM language, expand access for the different roles could be something like this:
Expand access to the left wheel is granted:
- to Designers working for project Standard, if:
wheel reference.V_maturity = PRIVATE and left wheel instance.owner = current user and left wheel instance.V_project = ‘Standard’
or:
wheel reference.V_maturity in {IN_WORK,WAITPP,SHARED} and left wheel instance.V_project = ‘Standard’ - to Leaders working for project Standard if:
left wheel instance.V_project = ‘Standard’
- to Reviewers working for project Standard if:
wheel reference.V_maturity = SHARED and left wheel instance.V_project = ‘Standard’
Expressed in the form of a rule in ENOVIA V6 language, expand access for the different roles could be something like this:
add rule VPLM_EXPAND
user VPLMDesigner
Read,Show
filter “((to.current == ‘PRIVATE’) && (owner ==
context.user) && (attribute[V_project] == ‘Standard’)) ||
(((to.current == ‘IN_WORK’) || (to.current == ‘WAITAPP’)
|| (to.current == ‘SHARED’)) && (attribute[V_project] == ‘Standard’))“
user VPLMLeader
Read,Show
filter "attribute[V_project] == ‘Standard’"
user VPLMReviewer
Read,Show
filter “(to.current == ‘SHARED’) && (attribute[V_project] == ‘Standard’))“