Data Authoring and Ownership Concepts | ||
| ||
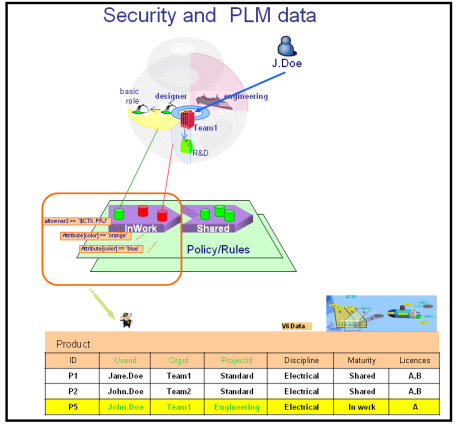
Policies and Data Ownership
A policy:
- may govern one or many types of PLM data
- defines a lifecycle process and associated events
- grants access rights with or without filters to assigned P&O users.
A rule:
- may govern one or more relationships and attributes
- grants access rights with or without filters to specific P&O users.
PLM data:
- is governed by only one policy
- possesses an ownership vector (userid, orgid, projectid) at creation time based on the selected login context
- may be transferred across users or organizations and/or projects.
![]()
How Is Ownership Set?
Data authoring and ownership are at the heart of security. It is important to understand how ownership of PLM objects is defined before progressing to a description of policies and rules.
The security context selected at logon sets the ownership for new data created. For example, user John Doe logs on using a specific security context and is authorized to create a product root: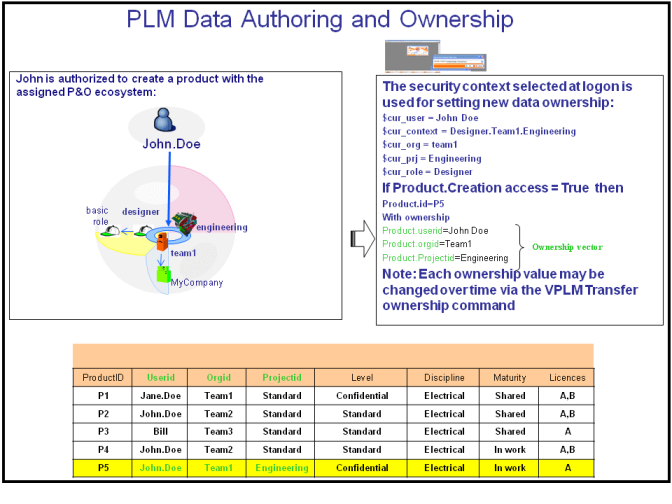
The product P5 when created is tagged with three ownership attributes:
- Userid
- Orgid
- Projectid.
This means that a variety of VPLM operations on data will only be authorized if the access rights corresponding to those operations are granted to the user.