Click the Check Access tab.
The following tab is displayed:
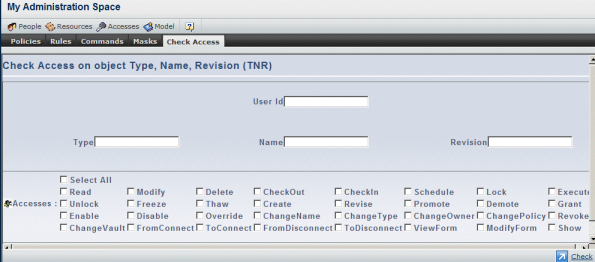
Specify the User Id of the user whose accesses you want to check, then click the Check command.
The Security context pull-down list is displayed listing the security contexts currently assigned to that user.
Select the appropriate security context from the list.
Enter the Type, Name and Revision of the business object.
For example, purely for the purposes of illustration:
- type: Person
- Name: DemoCreator
- Revision: -
Check the button for the Access(es) you want to check, or check the Select All button to select all accesses:
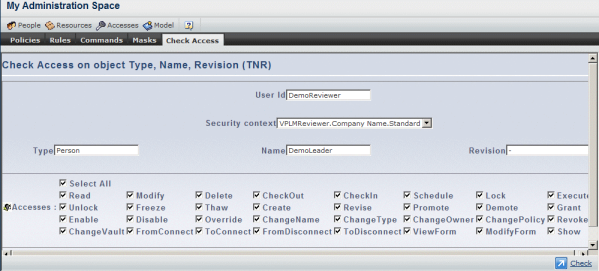
Several accesses may be selected at a time, in order to perform several checks at a time.
Click the Check button.
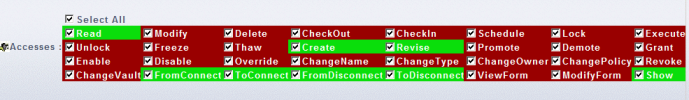
The output of the command is, for each selected access, a color-coded status indicating whether the specified user, when connected to V6 using the selected security context, is granted the specified access(es) on the V6 object or is denied access: red for denied, green for granted:
An error is displayed in case one of the input is invalid (e.g. the user or object doesn't exist).