Creating and Granting Customer-Defined Masks | ||
| ||
Creating User-Defined Masks
Let’s suppose you have a .metadata file defining modeller entities and their attributes that derive from PLMCORE metadata. For example: PLMProductDS.metadata.
You want to adapt the DEFAULT mask definition of the PLMProductDS modeller to designers to create a VPLMDesigner mask.
![]()
Granting the Masks Using the Business Administration Console
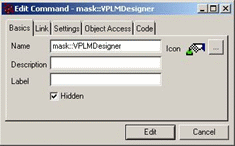
User-defined masks can only be granted by an ENOVIA V6 server-side command whose name is the mask name prefixed by:
mask::
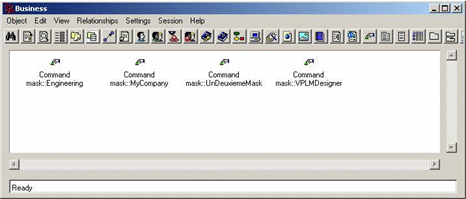
Once connected to the console, VPLM commands can be retrieved and selected:
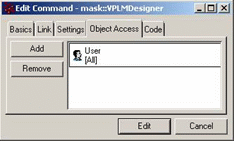
Their access can be modified according to your needs by adding/removing:
- P&O contexts, projects, roles or organizations (warning: all are stored as roles)
- Persons.
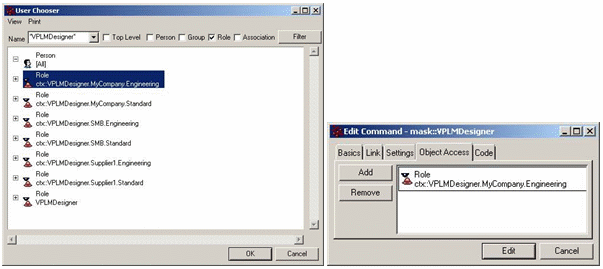
Their access can be modified in the Object Access tab of the Command editor, for instance, if you want to grant a VPLMDesigner mask to the context: ctx::VPLMDesigner.MyCompany.Engineering
![]()
Granting the Masks Using MQL
As with the Business administration console, the mask grant accesses can be created or modified using the modify command order in an MQL script.
Limitations.
Limitation 1: Indicative UI rendering via HTML does not take into account CATNls files for attribute aliasing.
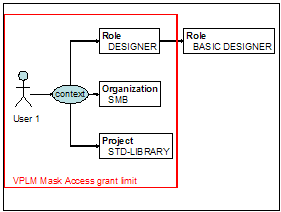
Limitation 2: Only masks granted on person, security context, and the first level of a security context's components (project, role, organization) are retrieved.
Suppose we have the following case:

Access to a mask MYMASK may be granted to:
- user1
- DESIGNER.SMB.STD-LIBRARY context
- DESIGNER role
- SMB organization
- STD-LIBRARY project
In these cases, User1 will use MYMASK (instead of DEFAULT).
But, it is useless to grant access to a mask to the BASIC-DESIGNER role, as this role is not directly connected to a context, ALTHOUGH it belongs to DESIGNER role's hierarchy.